Search Our Database
How to Check RDP Windows Server Connection Logs
Introduction
This guide explains how to check Remote Desktop Protocol (RDP) connection logs on a Windows Server. It focuses on identifying incoming RDP session activity using the built-in Event Viewer.
Prerequisites
Before you begin, ensure you have:
- Remote Desktop (RDP) access to the Windows Server
- Administrator privileges
Step-by-Step Guide
Method 1: Check Incoming RDP Logs Using Event Viewer
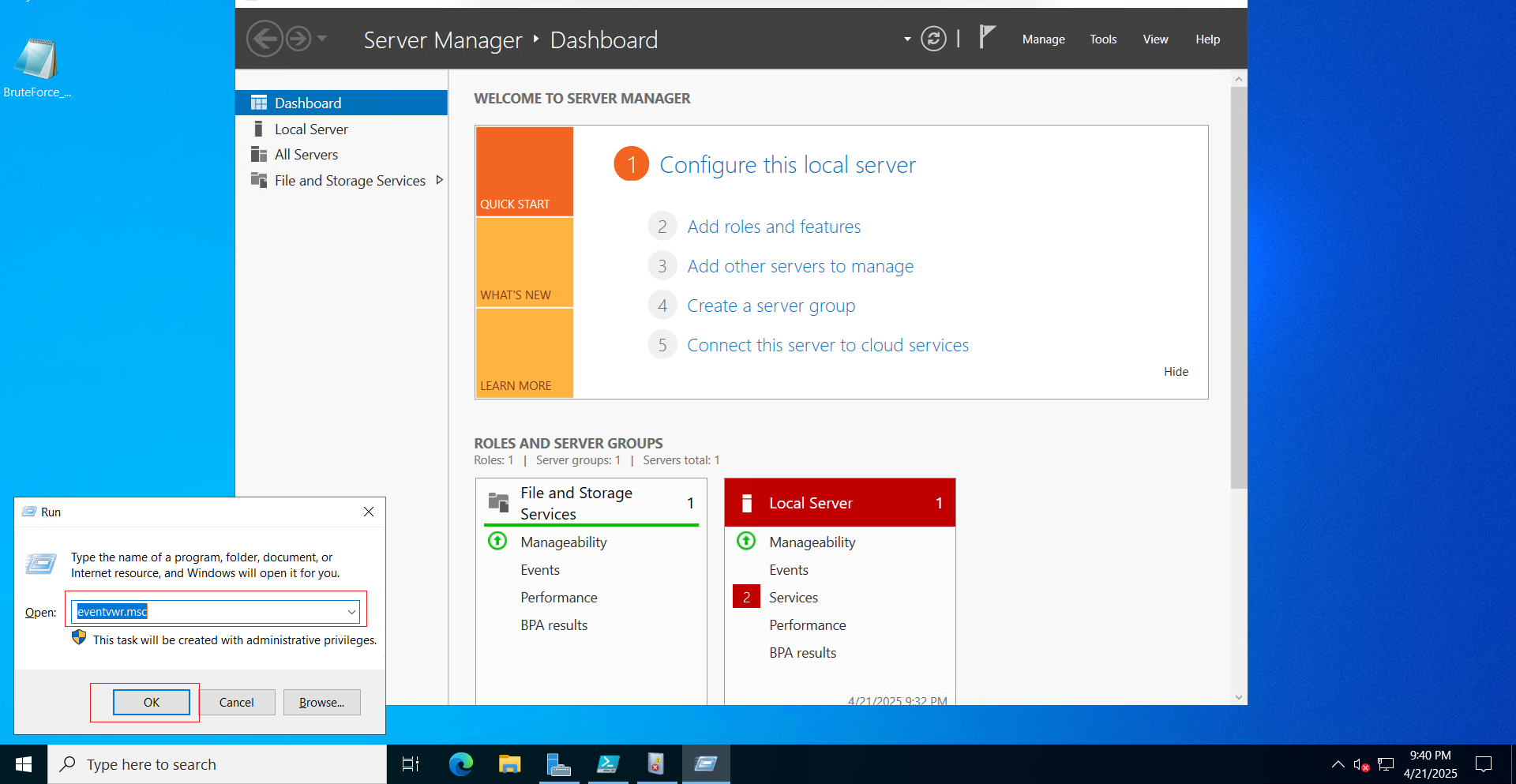
Step 1: Open Event Viewer
- Press 🪟 Win + R to open the Run dialog box.
- Type eventvwr.msc and press Enter.
Step 2: Navigate to the RDP Log Directory
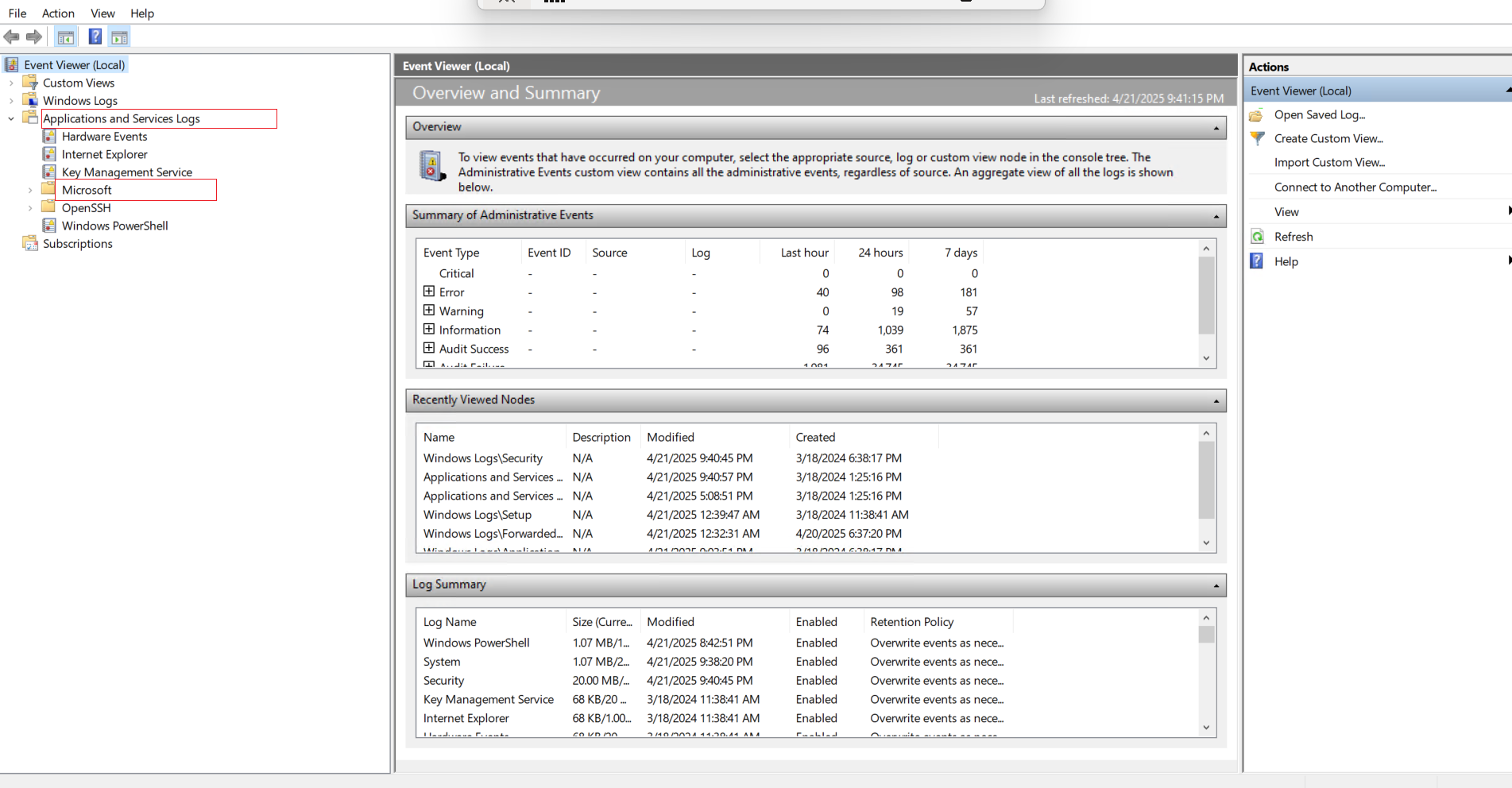
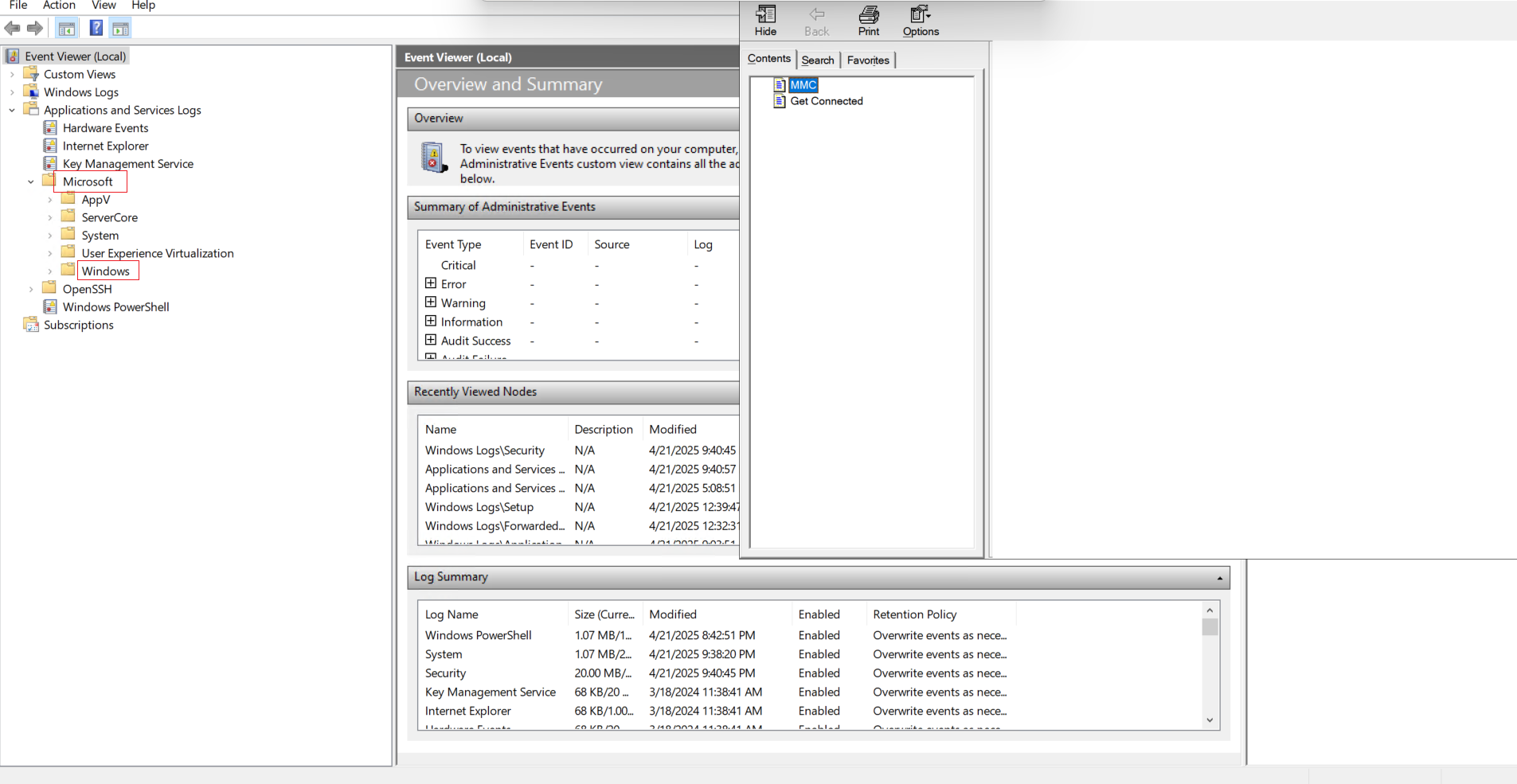
- In Event Viewer, navigate to:
Applications and Services Logs > Microsoft > Windows - Scroll down and select:
TerminalServices-RemoteConnectionManager > Operational - Right-click Operational and choose Filter Current Log.
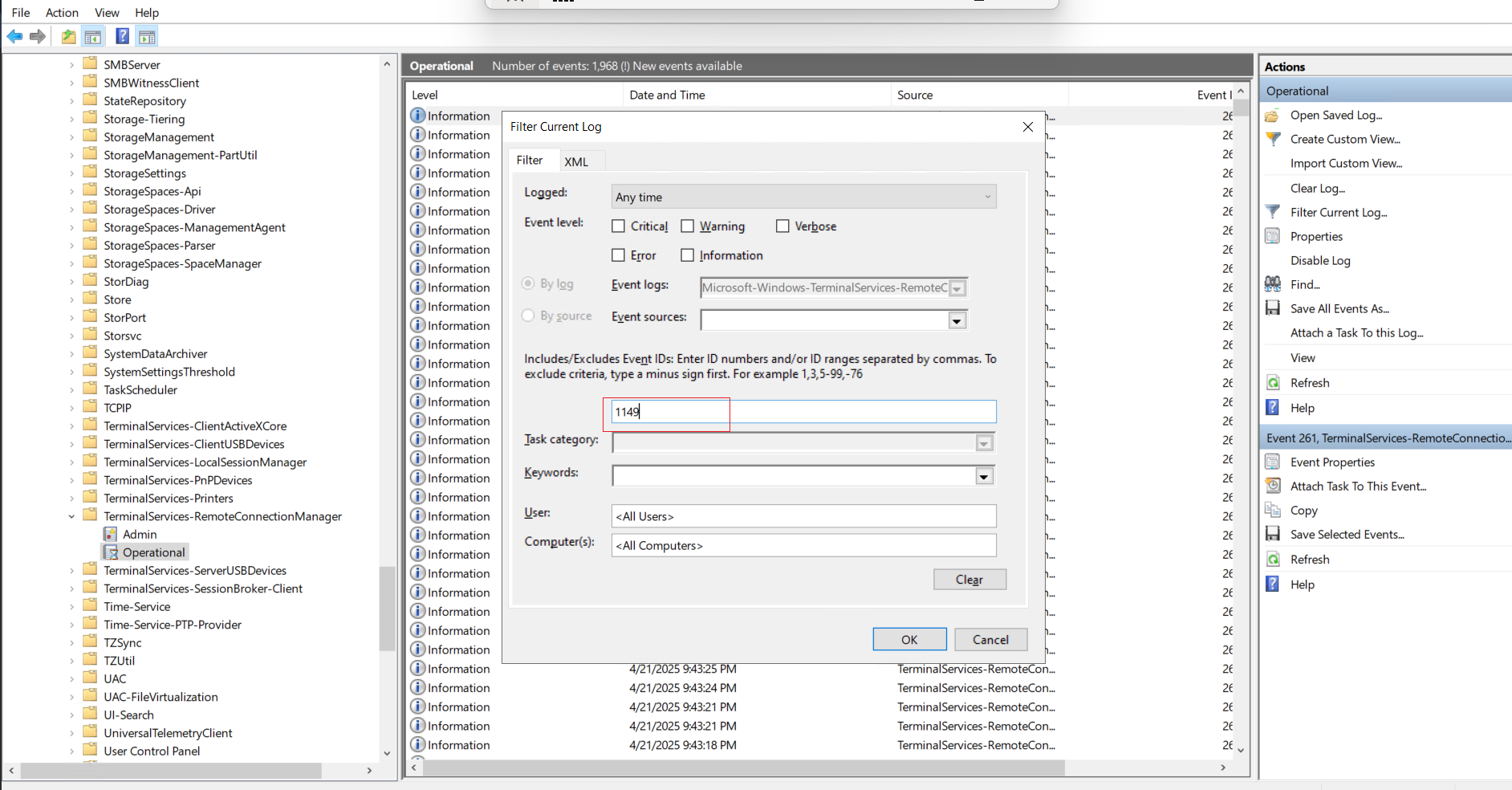
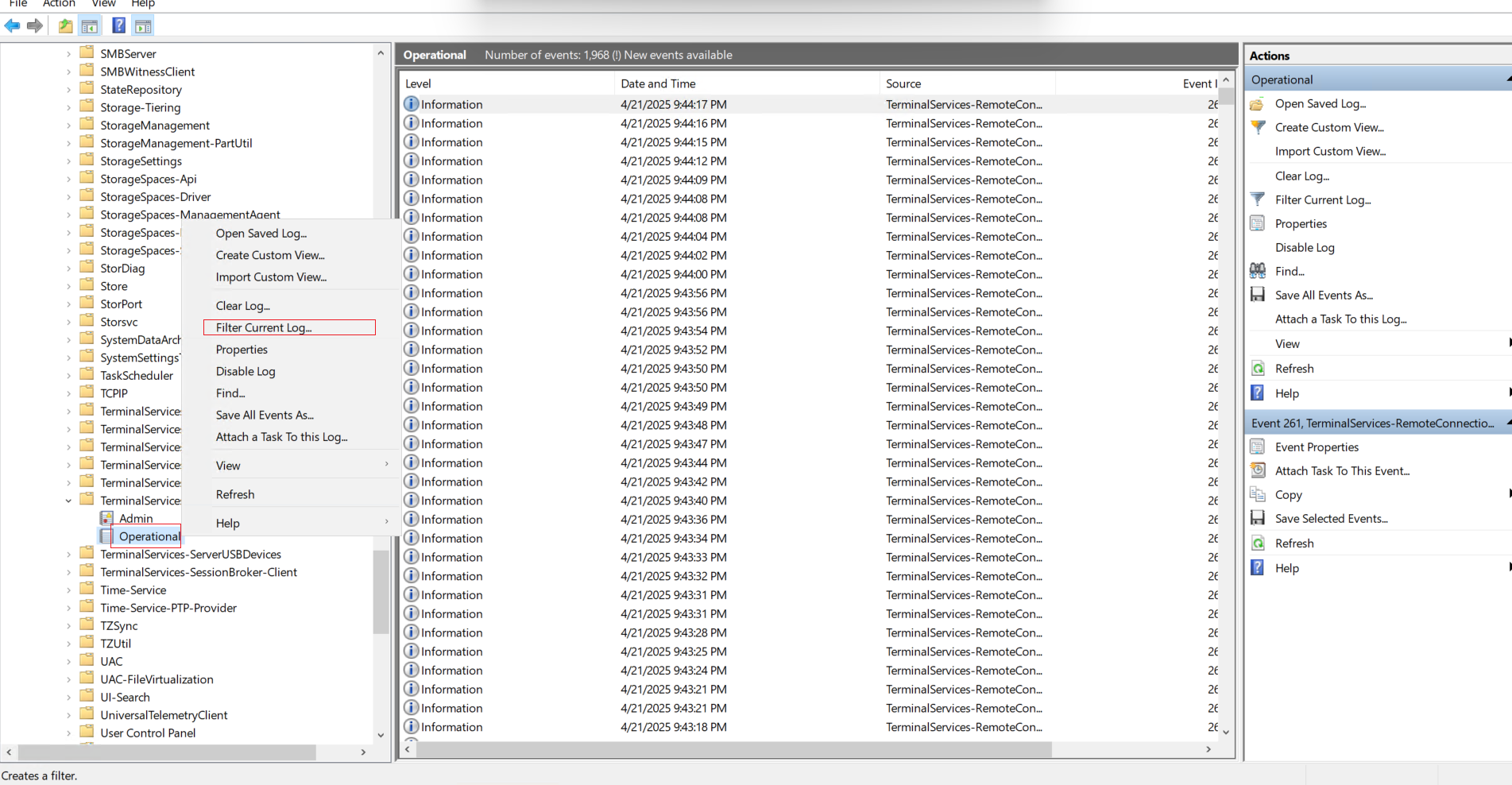 Step 3: Filter the Log by Event ID
Step 3: Filter the Log by Event ID
- In the Filter window, enter the Event ID: 1149
- Click OK to apply the filter.
Step 4: View the List of RDP Connections
You will now see a list of all historical RDP connection attempts made to the server.
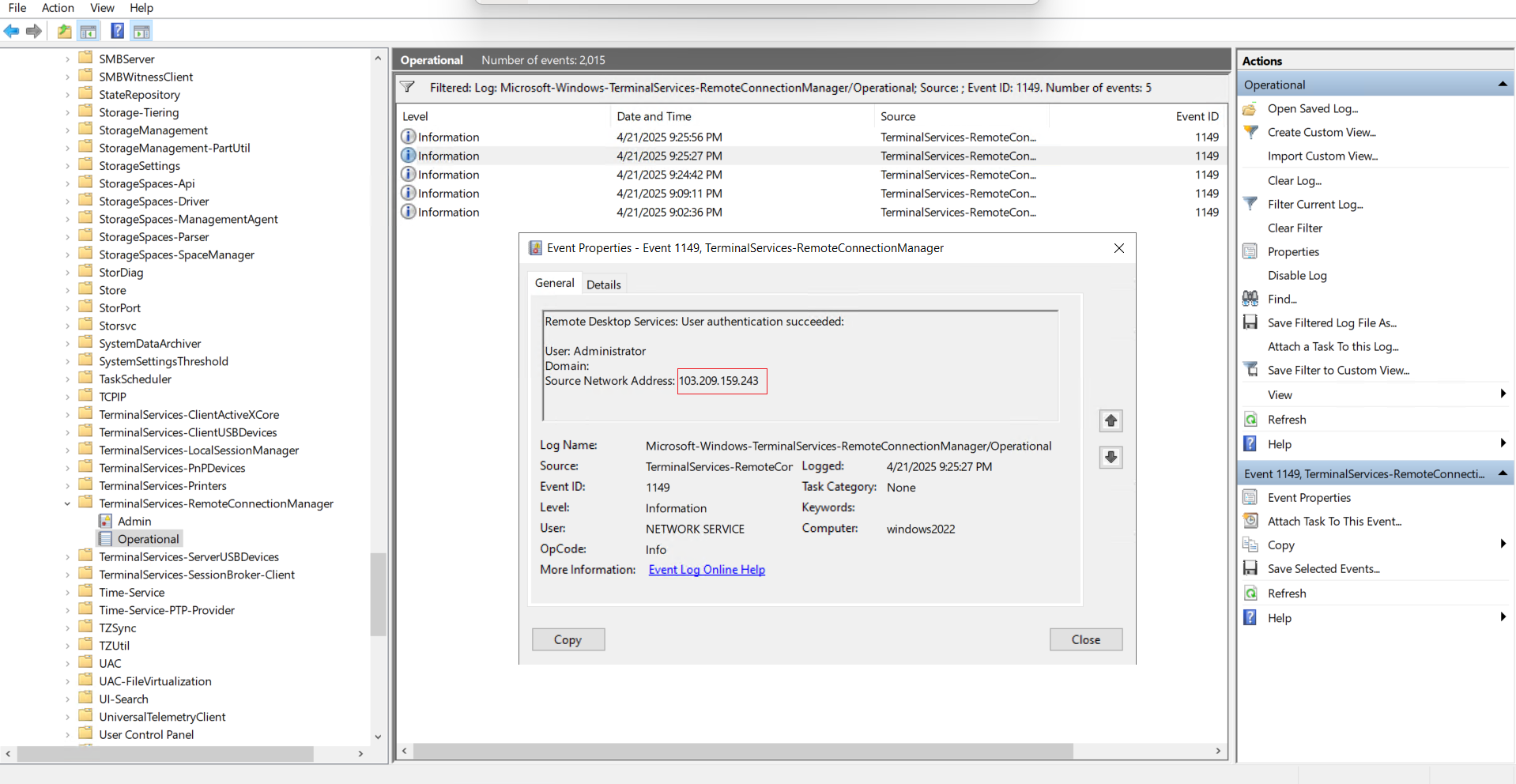
Step 5: Check Connection Details
Click any event log entry to view detailed information, including:
- Source IP address – You can use https://whatismyipaddress.com to look up unknown IPs.
- Login time
- The username
Conclusion
Monitoring RDP logs is critical for tracking access and safeguarding your server. By using Event Viewer and filtering for Event ID 1149 , you can quickly identify connection attempts and retrieve relevant information such as usernames and source IP addresses.
Regular log reviews help detect unauthorized access and improve security posture. If you encounter issues or need further guidance, please contact our support team at support@ipserverone.com. We’re happy to assist.