Search Our Database
Difference between a self signed and non self-signed SSL certificate
Introduction
SSL (Secure Socket Layer) is a security protocol that encrypts the data transmitted between a web browser and a server, preventing third parties from intercepting sensitive information. There are two main types of SSL certificates: self-signed and non-self-signed (CA-issued) certificates. Understanding the differences between these types is crucial in determining which one is more appropriate for your website’s needs.
A self-signed SSL certificate is generated by the owner of the website rather than a trusted Certificate Authority (CA). In contrast, a non-self-signed SSL certificate is issued and verified by a trusted CA. These two certificates differ in security level, trustworthiness, and practical application.
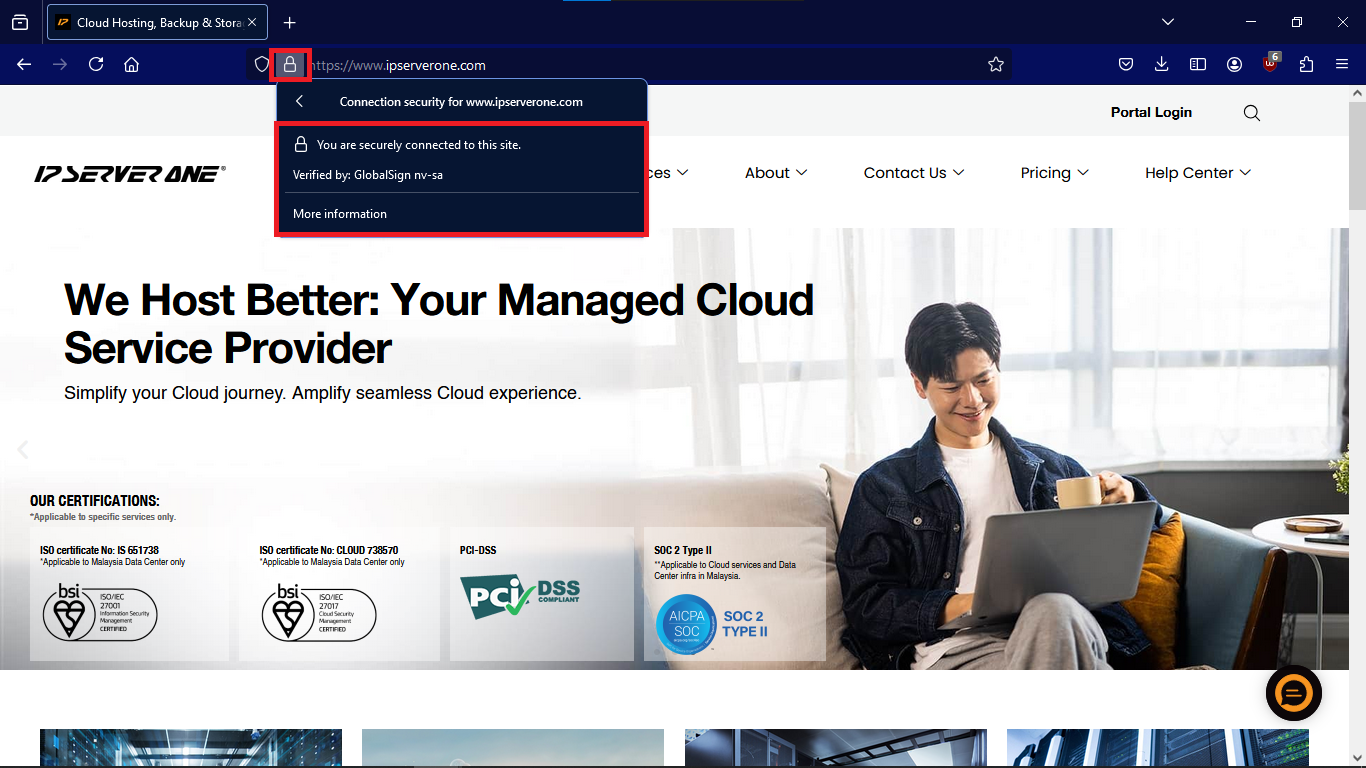
Difference between a self-signed and non-self-signed SSL certificate
1. Trust and Browser Warnings
- Self-signed SSL certificates: Browsers do not automatically trust these certificates because they are not verified by a CA. When a visitor accesses a website with a self-signed certificate, they will typically see a browser warning indicating that the connection may not be secure. This can discourage users from proceeding.
- Non-self-signed SSL certificates (CA-issued): Browsers recognize and trust these certificates as they are issued by a CA. Users will not see any warnings, and the website will display a secure lock icon, indicating that the connection is trusted.
2. Validation Process
- Self-signed SSL certificates: No validation process is involved. The website owner generates and signs the certificate.
- Non-self-signed SSL certificates: These certificates undergo a validation process, where the CA checks the legitimacy of the website owner. The level of validation can range from Domain Validation (DV) to more rigorous checks such as Organization Validation (OV) or Extended Validation (EV).
3. Cost
- Self-signed SSL certificates: These are free to create and use since no external CA is involved.
- Non-self-signed SSL certificates: Usually require a fee, which varies depending on the type and level of validation offered by the CA.
4. Support and Warranty
- Self-signed SSL certificates: No support or warranty is provided. The website owner is responsible for troubleshooting any issues.
- Non-self-signed SSL certificates: Typically include technical support from the CA or a reseller. In addition, many paid SSL certificates offer warranties in case of data breaches or certificate-related issues, sometimes covering damages up to millions of dollars.
5. Use Case
- Self-signed SSL certificates: Commonly used for internal or private services, such as local development environments or internal applications where the certificate is not meant to be public-facing.
- Non-self-signed SSL certificates: Ideal for public-facing websites, particularly those handling sensitive information, like e-commerce platforms or services that collect personal data.
Conclusion
Both self-signed and non-self-signed SSL certificates serve to encrypt website traffic. However, self-signed certificates are generally not recommended for public websites due to browser warnings and the lack of third-party validation. Non-self-signed SSL certificates, while involving a cost, provide enhanced trust, support, and security features that are crucial for ensuring a secure user experience.
For additional assistance or if you encounter any issues, please contact our support team at support@ipserverone.com.