Search Our Database
Disable DNS Recursion In Linux
Introduction
DNS recursion, when enabled, can be exploited in DNS amplification attacks, making it essential for server administrators to disable this feature if it is not required. DNS recursion allows a DNS server to resolve queries on behalf of other servers, which can make it a target for attackers aiming to leverage this capability in Distributed Denial of Service (DDoS) attacks. This guide will walk through the steps to disable DNS recursion on a Linux server using BIND, a commonly used DNS server software.
Prerequisites
- Access to the Linux server with root or sudo privileges.
- A text editor, such as vim or nano , to edit configuration files.
- Basic knowledge of navigating and editing configuration files in Linux.
Step-by-Step Guide
Step 1: Access the BIND Configuration
The main configuration file for BIND, named.conf , is usually located in either the /etc/bind/ or /etc/ directory. Use a text editor to open this file:
sudo vim /etc/bind/named.conf
Or, if the file is located in /etc:
sudo vim /etc/named.conf
Step 2: Edit the Configuration
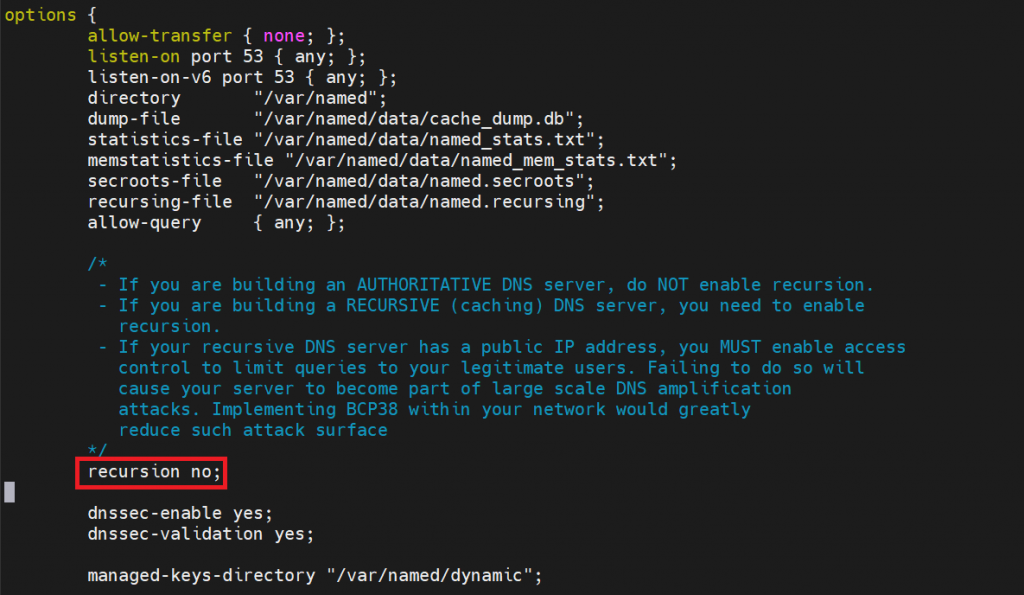
Locate the options section within named.conf (or the equivalent configuration file). Add the following line to disable DNS recursion:
recursion no;
Adding this line ensures that the DNS server does not perform recursive queries on behalf of other servers.
Step 3: Restart BIND to Apply Changes
To apply the configuration changes, restart the BIND service:
sudo systemctl restart bind9
Alternatively, rebooting the server will also apply the changes, though restarting the BIND service is typically faster and preferred.
Step 4: Test the Configuration
Verify that BIND is running correctly and that DNS recursion has been disabled:
sudo systemctl status bind9
To confirm that DNS functionality is working as expected, perform a DNS query test to ensure that the server is responding without recursion enabled.
Conclusion
Disabling DNS recursion on your Linux server is a critical step in securing your DNS infrastructure against DNS amplification attacks. By completing this configuration, you reduce the risk of your server being used as part of a DDoS attack. Always back up configuration files before making changes, and test your DNS server after applying new settings to confirm that it functions as intended.
Should you have any inquiries about the guidelines, please feel free to open a ticket through your portal account or contact us at support@ipserverone.com. We’ll be happy to assist you further.