Search Our Database
Generating Certificates and Users for OpenVPN on pfSense
Introduction
Creating a Certificate Authority (CA), server certificates, and user accounts is an essential process when setting up OpenVPN on pfSense. The CA is used to validate the OpenVPN server’s identity and authenticate user certificates, ensuring secure and encrypted communication. This guide provides step-by-step instructions for generating the Certificate Authority, server certificates, and user accounts creation and export user VPN configuration file, which are prerequisites for OpenVPN deployment on pfSense.
Prerequisites
Before beginning this process, ensure the following requirements are met:
- Access to the pfSense web interface with administrative privileges.
- A functional pfSense installation.
- Basic familiarity with certificate-based authentication concepts.
- Basic familiarity with OpenVPN configurations.
Step-by-Step Guide
Part 1- Generating Certificates
Step 1: Generate the Certificate Authority (CA)
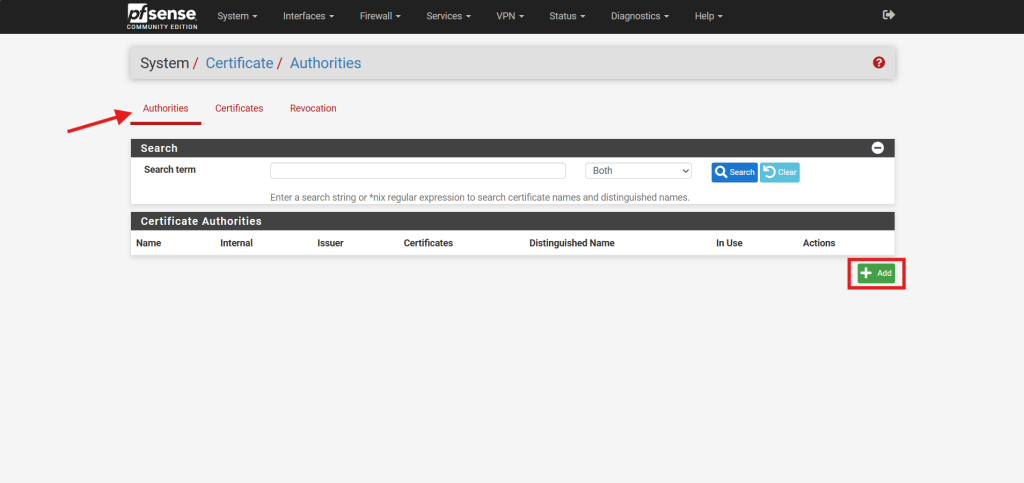
- Navigate to Certificate under System in the pfSense web interface.
- Click the Add button at the bottom right to create a new CA under Authorities.
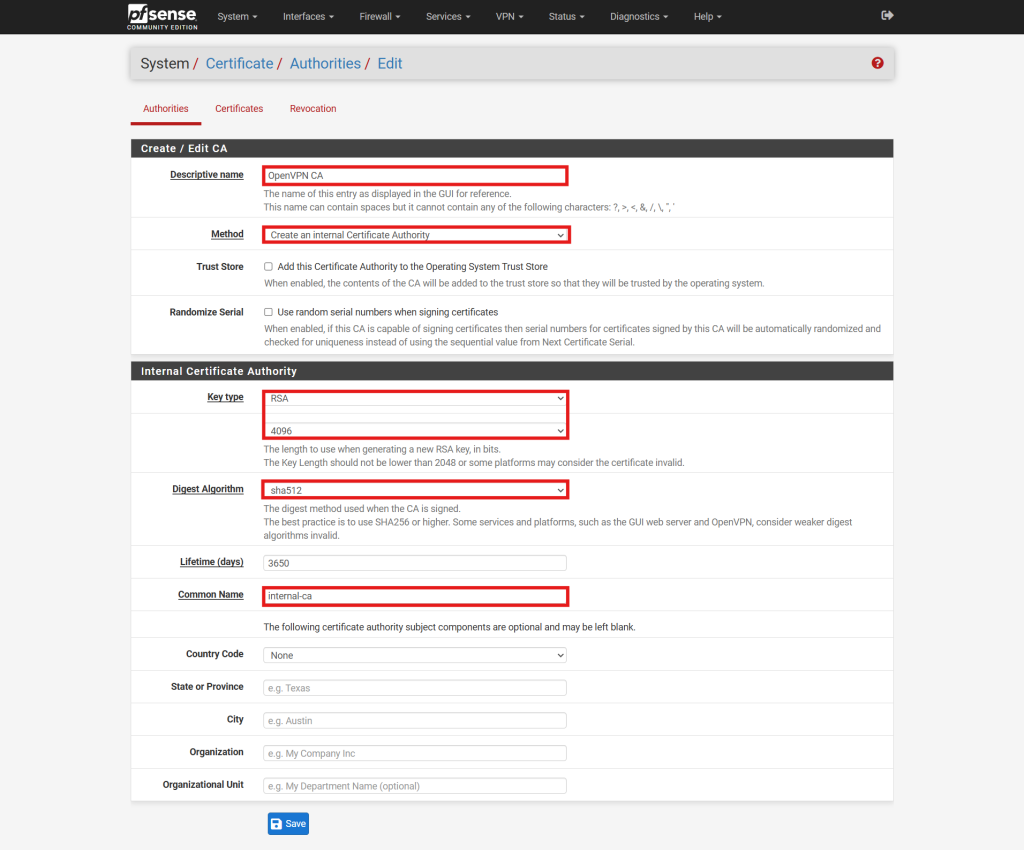
- Configure the CA with the following parameters:
- Name: Enter a descriptive name for the CA.
- Method: Set to Create an internal Certificate Authority.
- Key Type: Select RSA or ECDSA. For this example, RSA is used.
- Key Length: Choose a minimum of 2048. For enhanced security, 4096 is recommended.
- Digest Algorithm: Use at least sha256. For this example, sha512 is selected.
- Common Name: Enter a name for the certificate, or use the default internal-ca.
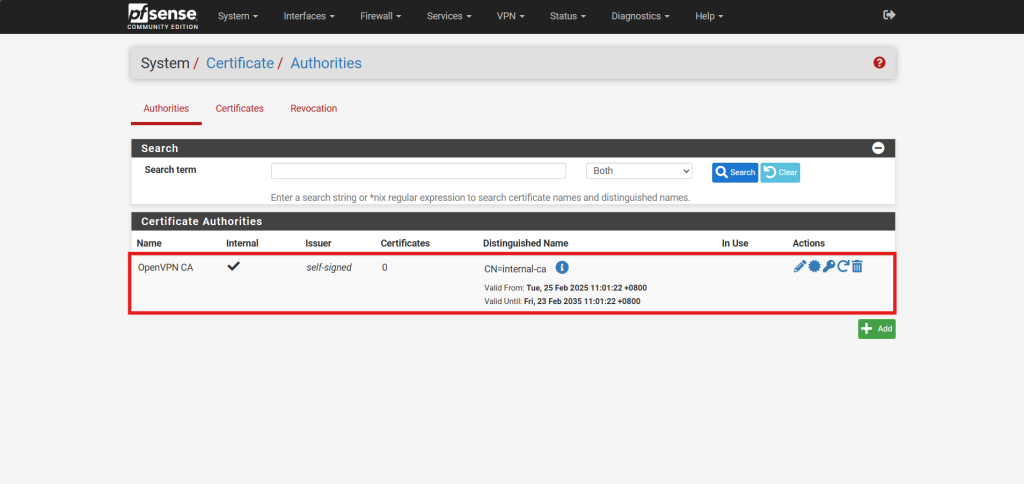
- Click Save to generate the Certificate Authority.
Step 2: Generate the Server Certificate
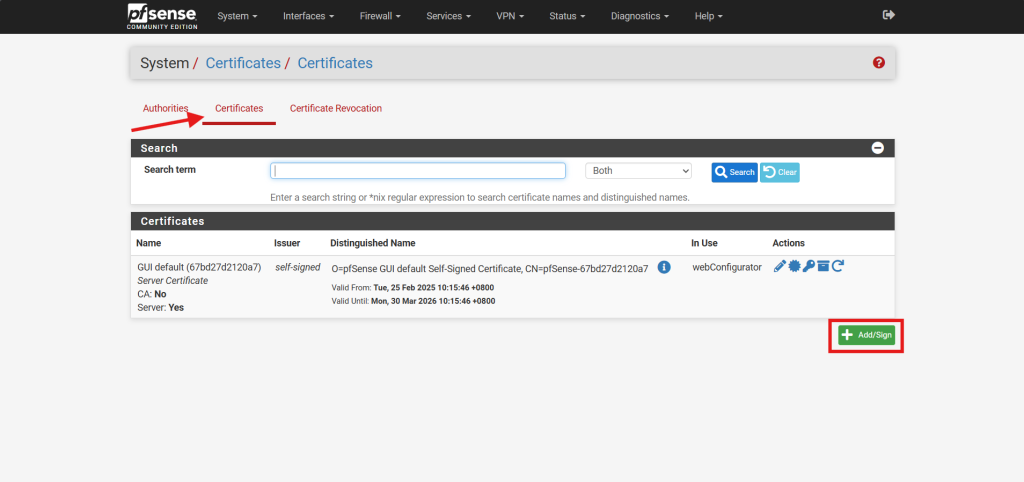
- Navigate to Certificate under System and select the Certificates in the pfSense web interface.
- Click the Add/Sign button at the bottom right to create a new server certificate.
- Configure the server certificate with the following parameters:
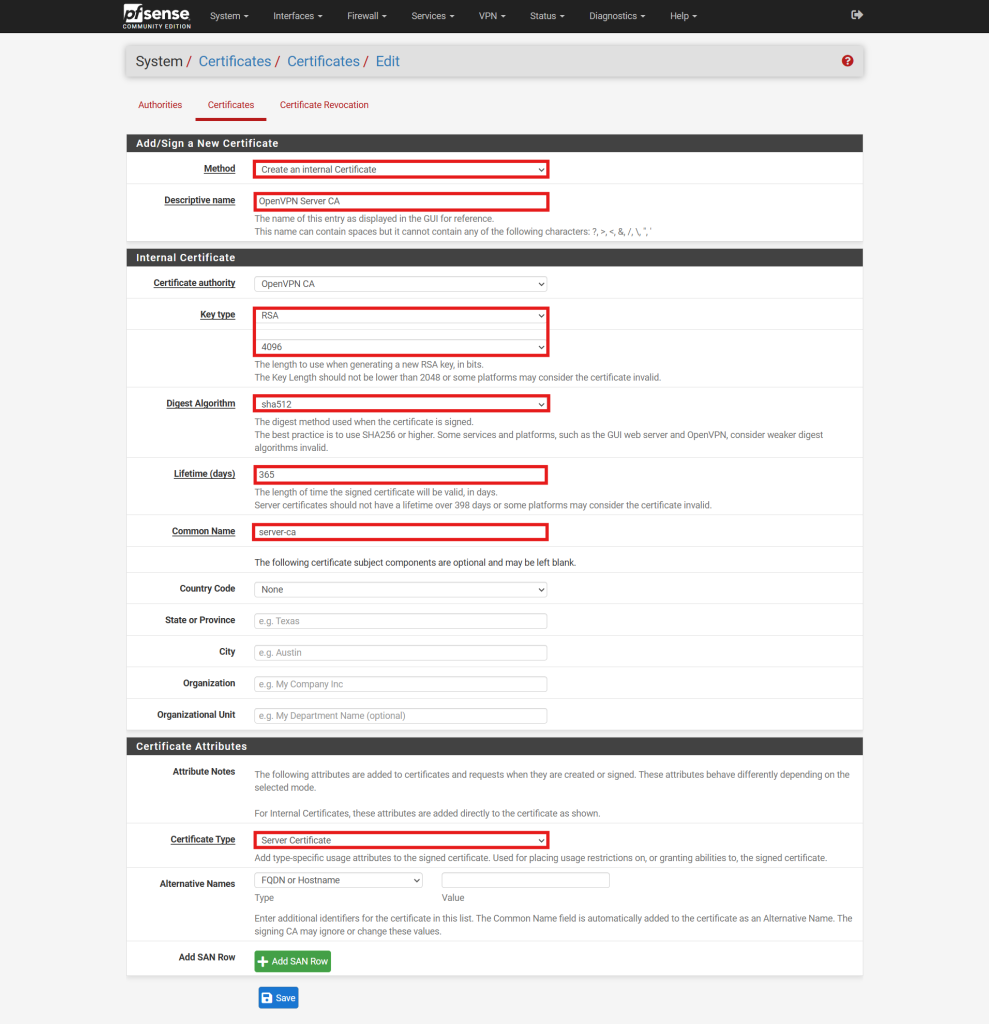
- Method: Set to Create an internal Certificate.
- Descriptive Name: Provide a meaningful name for the certificate.
- Key Type and Length: Use the same values selected for the CA (RSA with 4096 bits in this example).
- Digest Algorithm: Match the value set for the CA (sha512 in this example).
- Lifetime: Set to 365 days or a preferred duration.
- Common Name: Enter a name for the certificate, or use the default internal-ca.
- Certificate Type: Choose Server Certificate.
- Click Save to generate the server certificate.
Part 2 – User Creation
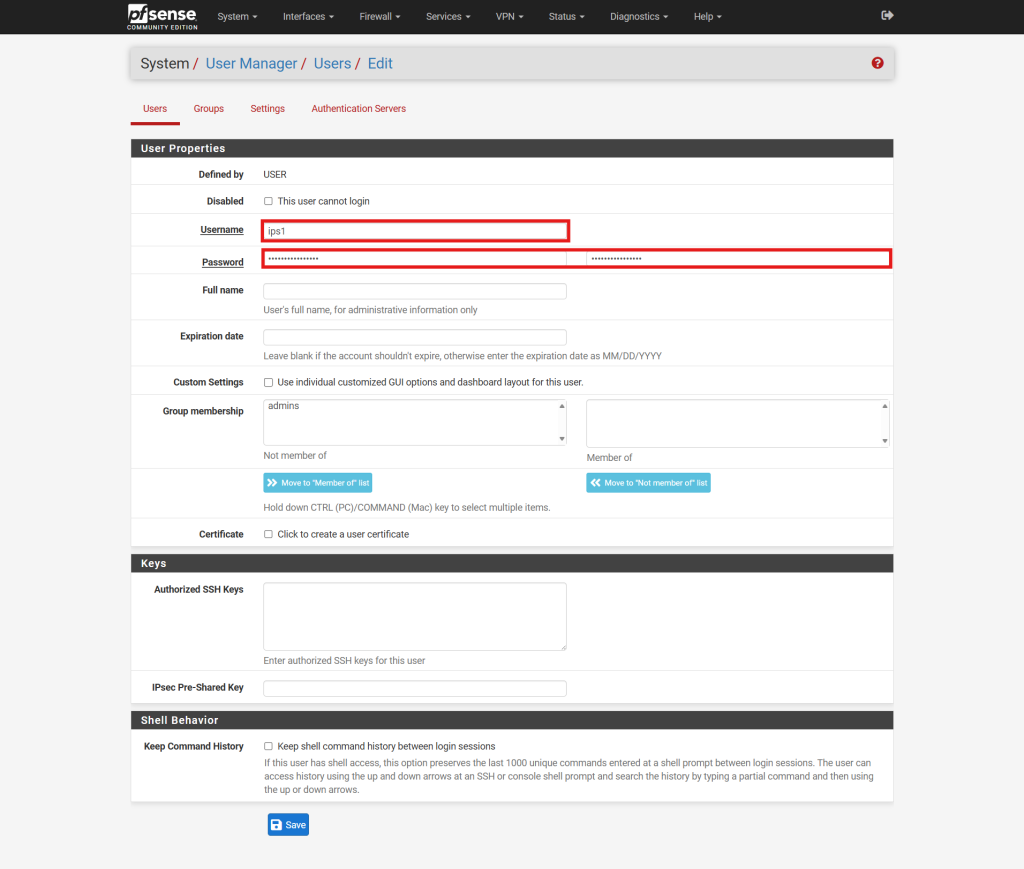
Step 1: Create a New User
- Log in to the pfSense web interface using administrative credentials.
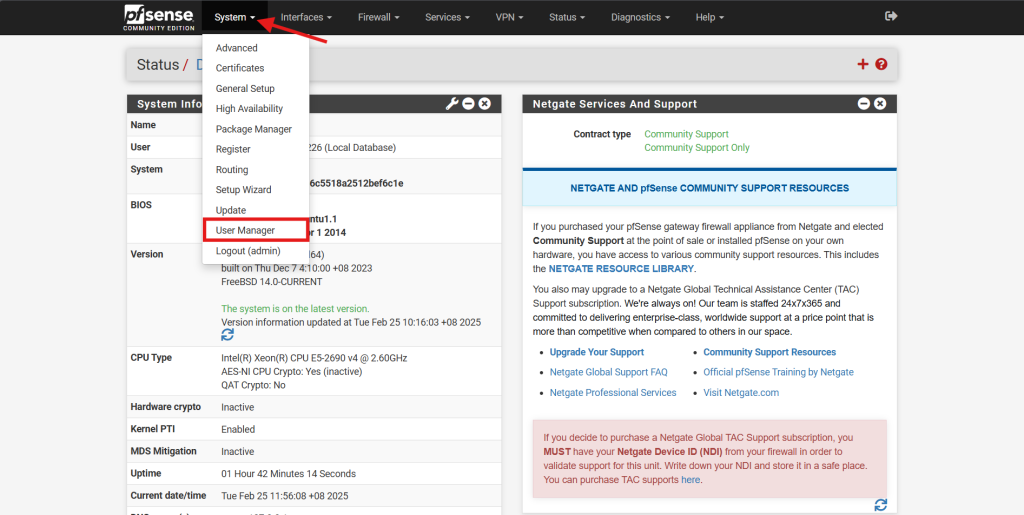
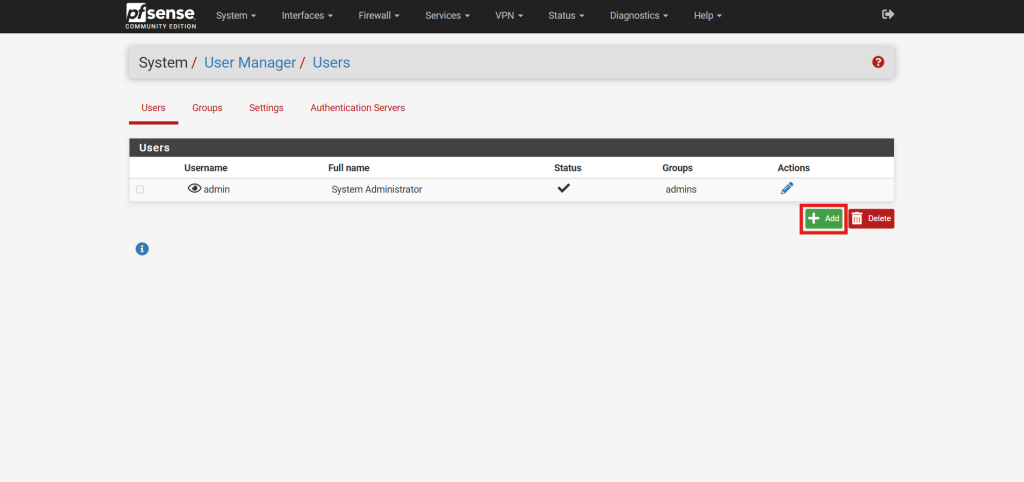
- Navigate to User Manager under System.
- In the User Manager, click the Add button to initiate the creation of a new user account.
- Fill in the following fields:
- Username: Enter a unique identifier for the user.
- Password: Input a strong password for the user account.
- Full Name: Optionally, provide the user’s full name for identification purposes.
- Expiration Date: If applicable, set an expiration date for the account.
- Group Memberships: Assign the user to appropriate groups, such as admins or users, based on the required access level.
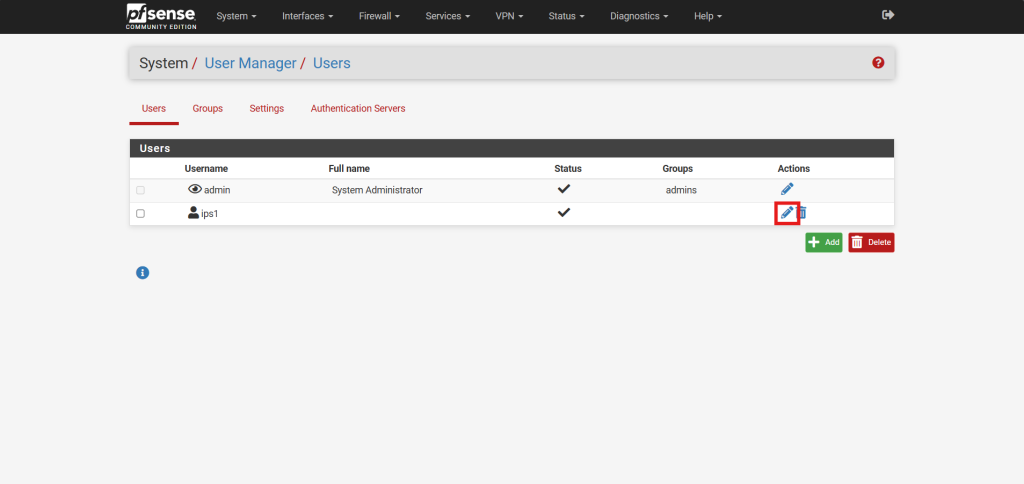
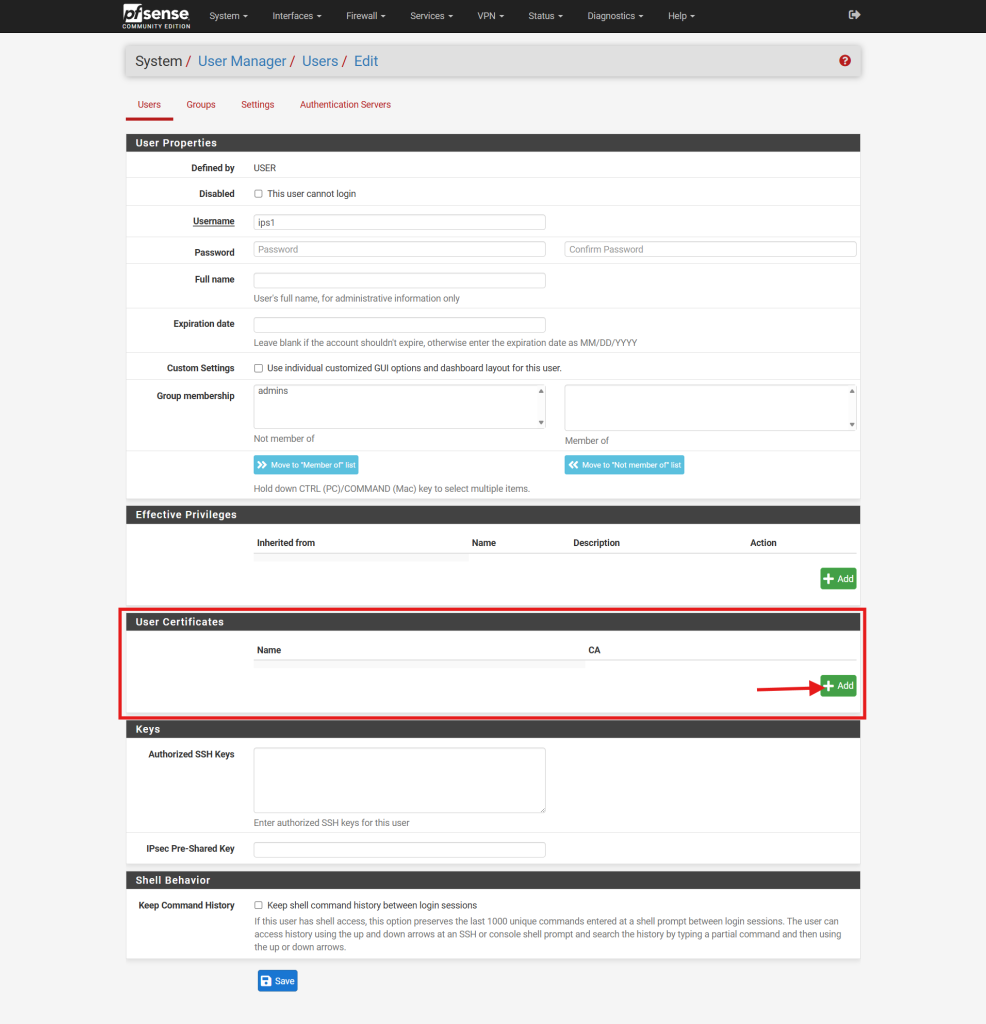
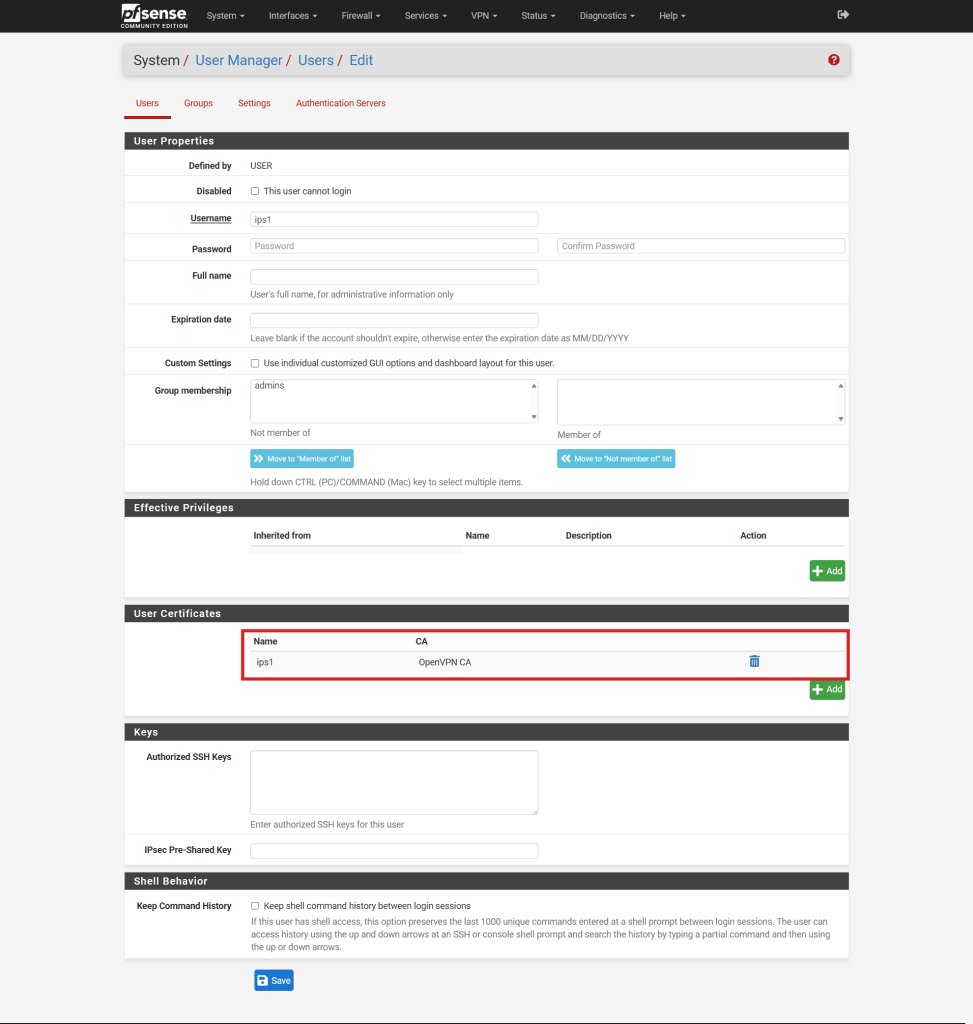
Step 2: Generate a User Certificate
- If you chose to set up your server for certificate-based authentication or for certificate and password-based authentication, click the pencil icon to the right of your new user.
- Locate User Certificates and click the Add button to create a new certificate for the user.
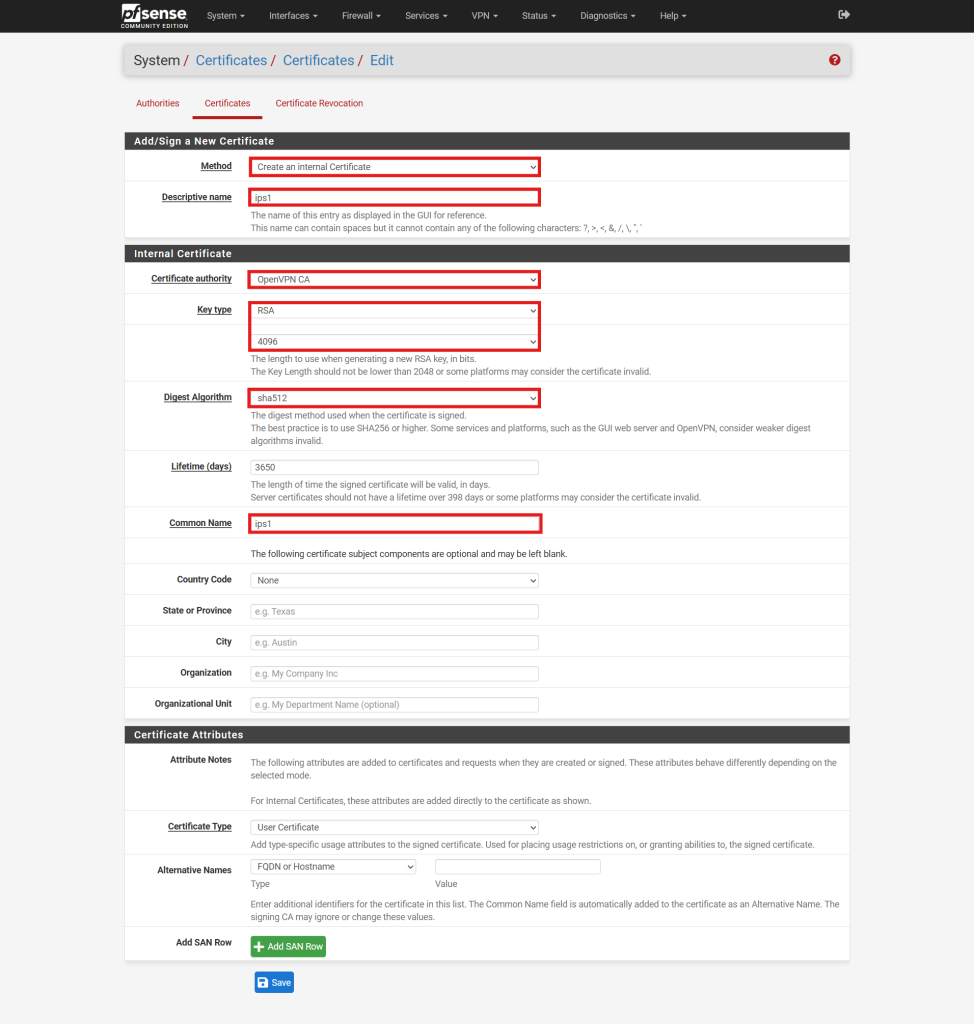
- In the certificate creation form, provide the following details:
- Method: Set to Create an internal Certificate.
- Descriptive Name: Assign a name to the certificate, typically matching the username for clarity.
- Certificate Authority: Select the CA associated with the OpenVPN server.
- Key Type: Choose the desired key type (e.g., RSA or ECDSA) and specify the key length or curve.
- Lifetime: Set the validity period for the certificate, commonly 3650 days (approximately 10 years).
- Common Names: Assign a common name to the certificate, typically matching the username for clarity. **Having same common name will causing conflict on the certificate and users will face connection issue.
- Click Save to generate the certificate.
- After configuring the user details and generating the certificate, you will see the certificate is generated, click Save to create the user account.
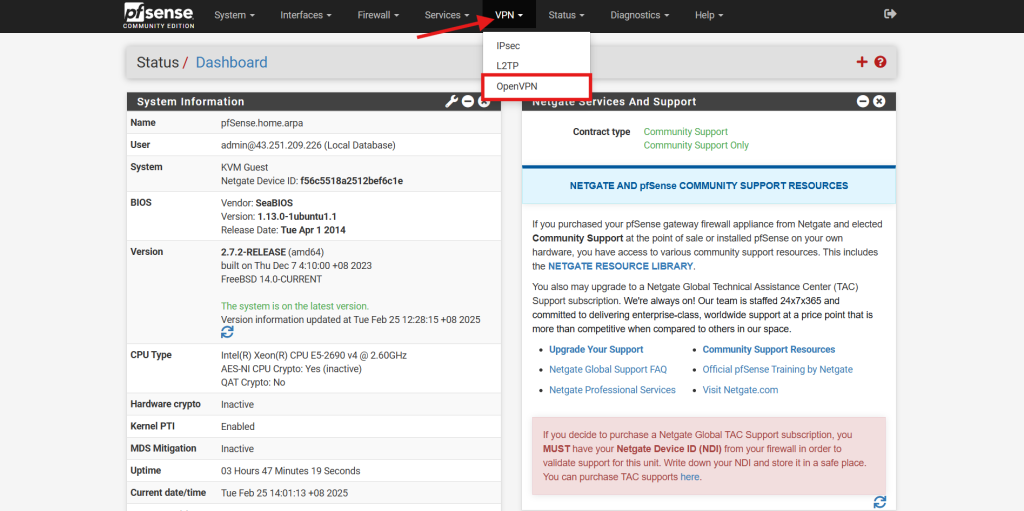
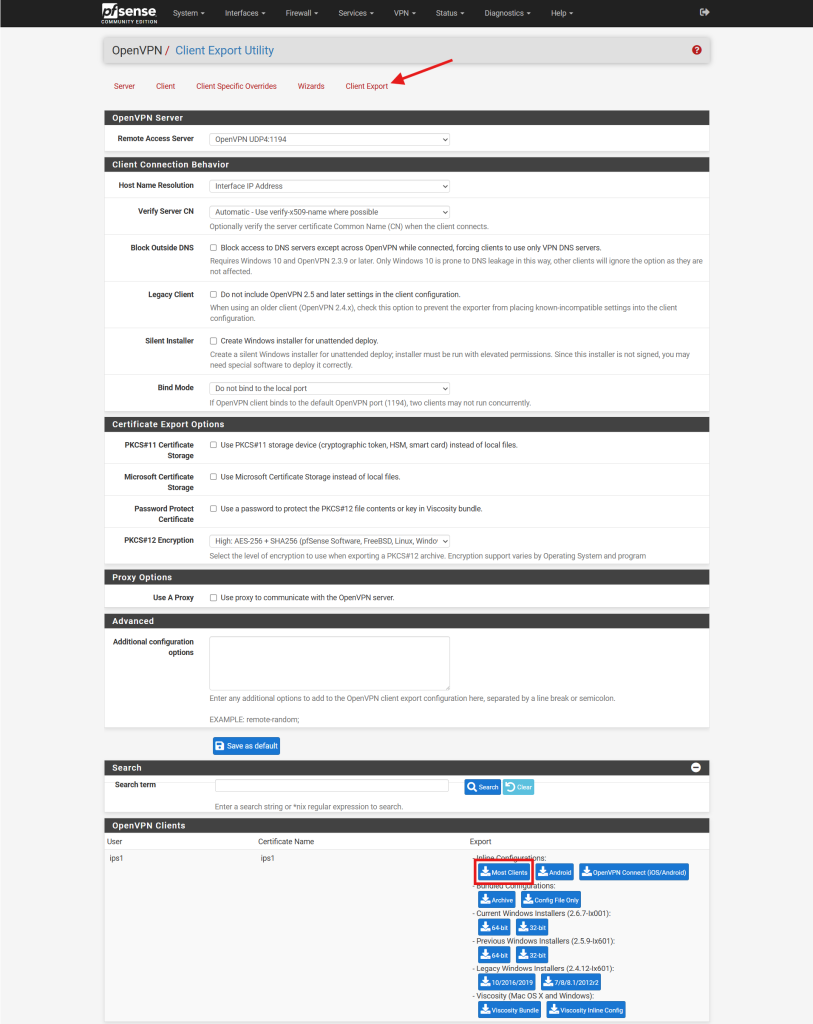
Step 3: Export user VPN configuration file
- Navigate to OpenVPN under VPN.
- Navigate to Client Export, and scroll to download the user VPN configuration file.
Conclusion
By following this guide, administrators can effectively create and manage user accounts for OpenVPN on pfSense, ensuring secure and controlled access to the network. Proper user management is essential for maintaining the integrity and security of the VPN environment.
Should you have any inquiries about the guidelines, please feel free to open a ticket through your portal account or contact us at support@ipserverone.com. We’ll be happy to assist you further.